- Dec 10, 2025
Share this post on:

IoT is one of the modern trends with immense popularity that seamlessly connects and communicates via the Internet.
According to stats, in 2022, the market for IoT is expected to grow 185 to 14.4 billion active connections. By 2025, IoT-connected devices can reach 27 billion.
With technological advancement, you can include and connect any device to IoT. With time, more devices are connecting to the Internet, and there is always a potential for a cyber attack.
The leading concerns include software vulnerabilities and cyber attacks that make organizations think before implementing IoT solutions for their organizations. It is vital to ensure the best practices and security measures that protect the devices from getting hacked and protect the data for easy transmission.
Even though users can connect their devices to the work network, it enhances the risk of attack.
For example, if you synchronize a fitness tracker with a smartphone, further connected to your corporate network. It allows hackers to barge into the organization's security. Therefore, implementing the best security practices for your IoT ensures security.
What are IoT and IoT security?
IoT generally refers to a network of devices that are easier to connect. These devices streamline data exchange without human interference.
And IoT security is protecting devices and networks from the potential risk of cyberattacks and breaches. You can achieve it by identifying and addressing the vulnerabilities and implementing the best IoT practices that keep the IoT system safe. Let us discuss the components IoT uses to exchange and process data.
1. Smart Devices
It collects, store, and share data regarding the environment, devices, and related components.
2. Embedded Systems
These are systems used by intelligent devices, which include processors and sensors with the ultimate goal of collecting, sending, and acting on data acquired by different environments.
3. IoT Gateway
It routes the data between the IoT devices and the cloud.
4. Cloud Data Centre
It simply makes data exchange easier with the remote servers via a wireless connection.
Importance of IoT Security
IoT devices are connected and further connected with the Internet. Whether it is about enhancing road security, boosting car performance, home, or others, IoT has been offering the most effective solutions that enhance our working style and lifestyle.
IoT ensures the integrity and confidentiality of your data, eliminates any malware, and mitigates the risk of any vulnerabilities. The two ultimate aim of IoT security includes:
- Ensuring to collect the data, process, storage, and transfer with security and confidentiality.
- Depicting and eliminating any sought vulnerabilities in the IoT environment.
IoT Security Threats in 2023
As we have already mentioned, every device is connected and linked to the Internet. So if one device gets hacked, the hacker can access all your devices. But, before moving further in the article, let us first learn about the security threats of 2023.
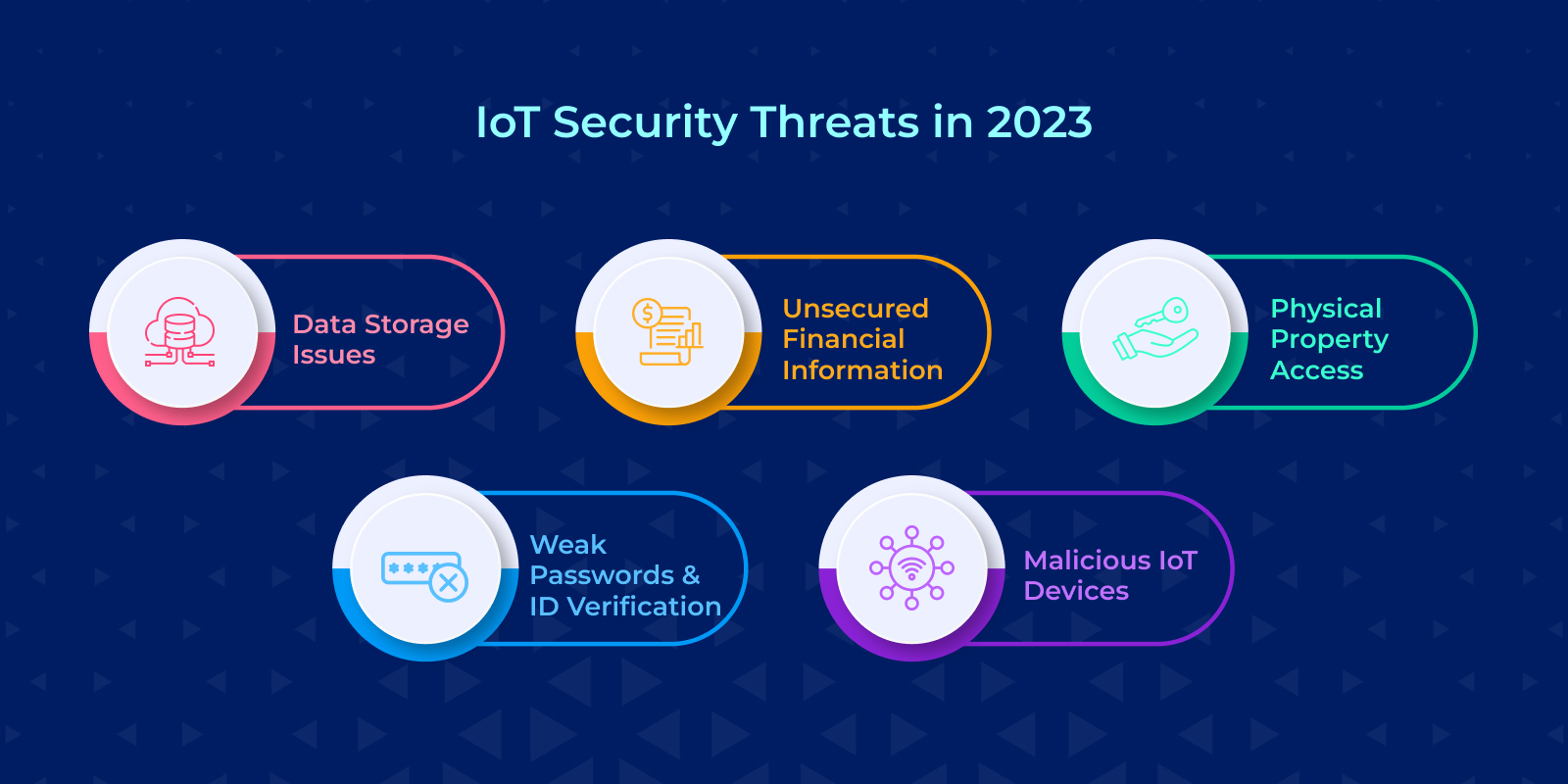
Data Storage Issues: IoT devices store all the data they collect in the cloud. It makes data more prone to be hacked or to become a target for other cybercriminals if it is not suitably secured. So it is crucial to transfer data with an encrypted connection. But many IoT devices do not have reliable firewalls and other reliable security features. So this is one of the biggest threats to IoT security.
Unsecured Financial Information: IoT devices have the financial information of their users stored in them. The financial information involves credit card details or banking information, which makes it more vulnerable to becoming a target for hackers. It is one of the reasons that you should be aware of MQTT TLS configuration.
Physical Property Access: There are many IoT-connected physical properties such as homes, locks, cars, and more IoT-connected devices. If someone hacks your IoT device to which your physical property is connected, they can easily access the physical property too.
Weak Passwords and ID Verification: The biggest problem is that many IoT devices are not strong password protected. But, the set passwords are easy to guess and hack. However, many IoT devices use other forms of identification for identity verification, like fingerprints and facial recognition as a form of identity verification.
Malicious IoT Devices: IoT makes communication through electronic devices easy. But it has made it easy for cybercriminals to infiltrate IoT networks. Not only that, it has made it easy to make IoT devices more prone to run some malicious bots and transfer the virus, which can be harmful to your financial and personal security.
Focusing on the IoT Security Challenges
Unlike the traditional approach, which involves secure hardware or software, IoT focuses mainly on eliminating cyber and physical convergence.
Let us quickly find out the challenges and concerns for the businesses.
1. Lack of testing and development
It is crucial to consider security practices before bringing the products into the market. Developers may have overlooked the device security during the development process, but once you launch it, there is a lack of updates. Therefore, businesses must be aware of IoT security and give it prominence importance.
2. Malware and Ransomware Risks
As there is an exponential boost in the IoT interconnected devices, the potential risk of malware attacks and ransomware increases too. Most devices face IoT botnet malware, a common variant seen.
If the attackers get the opportunity to inject the malware into the IoT system, they may change its functionality, spoil and collect all your data and disable the features.
3. Concern with Data Leakage
When the IoT stocks are up, a large amount of user data is gathered, transmitted, and processed. It enhances the risk of data leakage.
4. Escalated Cyber Attacks
Due to limited processing power, all IoT devices are highly vulnerable to denial-of-service attacks (DoS). These devices act as an attack base that infects more and more systems for malicious activity. The DoS attack on IoT devices commonly affects organizations and IoT homes.
5. Insecure Interface
The most common issues with the interface that ultimately affects IoT devices are encryption or inadequate data authentication.
6. Increase Remote Working
The pandemic led to an effect on the economy and changing trends. One of them is remote working. While IoT devices help many users to work from home, the home network may lack the security of organizational networks. With the increased usage, the risk and cyber vulnerabilities increase.
Best Practices that help Improve IoT Security:
Businesses must consider the security implications before moving forward with the process, and here are the best IoT practices that help enhance IoT security.
1. Secure Smart Devices
-
Tamper-resistant hardware is a must
To steal and access sensitive user data, the attackers can target the devices with long-lasting effects. To safeguard crucial data, it becomes vital for businesses to integrate tamper-resistant hardware that disables their product when attackers try to tamper your products. -
Constant Updates
Offering product security is vital, as there are a lot of updates and patches. These updates have nothing to do with the end user, and you can plan for automatic and mandatory security updates. The updates develop when you release the system automatically. And businesses must ensure to keep an eye on upcoming vulnerabilities. -
Thorough Testing
Testing helps in identifying the vulnerabilities and reducing the attack surface quickly. Businesses can use static code analysis to know the flaws and use dynamic testing to know the vulnerabilities further. -
Device Data Protection
IoT devices must ensure data security both during and after exploitation. So, ensure disposal of the used products or a way to discard them without exposing sensitive data.
2. Secure networks
-
Robust Authentication
Strong authentication can be achieved easily with a unique set of default credentials. You must use the latest protocols that ensure they keep going for a longer time. You can ensure offering the product with two-factor or multifactor authentication.
-
Encryption and Secure Protocol
IoT is all about communication between devices, so it is a must to provide security. The cryptographic algorithm must be adopted to restrict the capacity of IoT devices. With an IoT architecture, you can use technologies like RFID, Bluetooth, Ethernet, and more.
-
Segregate the network into segments
Implementing firewall security helps in the separation of large networks into smaller ones. Different ranges of IP addresses or LANs can ensure easy segregation, and to have a secure internet connection, you need to implement a VPN to your IoT system. You can also explore Cybernews’ NordVPN vs Surfshark comparison, which helps you evaluate two of the most secure VPN options for protecting segmented networks and IoT environments.
-
Reduce the bandwidth of the device
Restrict the network traffic to the necessary amount for the proper functioning of the IoT device. Program device to limit hardware and kernel-level bandwidth. It eliminates the possibility of a DoS attack.
3. Secure your data
-
Protects sensitive data
You must have set a unique default password for all your products differently. When you use the device for the first time, update the password immediately. With robust authentication, only limited users get access to the data. Going that extra mile for more privacy and protection, you can implement a reset that allows the deletion of sensitive data and configuration settings. -
Collecting only crucial data
Ensure the collection of the data that is mandatory for its operation. It prevents data leaks, safeguards consumer data and privacy, and eliminates the risk of non-compliance with protection and standards. -
Keeps Network communication safe
To ensure better security and privacy, you must limit the unnecessary communication of your product within the IoT network. Do not close your eyes and rely on the network firewall only, but make the product invisible via inbound connections by default.
Quick Examples of IoT Security Breaches
Let us quickly get through a few examples of IoT devices that were compromised by criminals recently.
1. Mirai Botnet Attack in 2016
Botnet usually refers to a computer network infected by malware. It performs an automated task without bringing it to your knowledge. It pulled thousand of connected devices into Botnet, called Mirai. As a result of this attack, several websites, including Spotify, PayPal, and more, were shut down temporarily.
2. VPNFilter Malware 2018
It was one of the attacks that infected over half a million routers in around 50 countries, often targeting devices by exploiting vulnerabilities exposed through unsecured access points a reminder of how important it is to regularly check details like what is my IP and location to detect unusual activity or unauthorized access. The malware is powerful and gets installed on router-connected devices. It also collects information passing through, blocks the network traffic, and sneaks away your sensitive passwords.
3. Tesla Model X 2020
Cybersecurity experts hacked the Tesla Model X in simply 2 minutes by using its Bluetooth vulnerability. Many other cars rely on wireless keys and have experienced a similar attack.
4. Verkada Camera Feed 2021
It is a security camera firm, hacked in 2021. Swiss hackers compromised its 150,000 live camera feeds. The cameras monitored the activity in the public sectors buildings like schools, hospitals, and other organizations.
How can ToXSL help?
With the growth of IoT, it is crucial to eliminate security risks that come the way of the developers. For both users and businesses, the technology has high-end value, and by securing IoT solutions, you can protect your business and customers.
You must take care of the security issues from the earliest, which means from the research phase itself. ToXSL is one of the leading providers of IoT services that seamlessly help businesses and other organizations to keep their devices and network secure from security threats.
From enhanced security measures to controlled IoT devices, you can enable your organizations to block unknown devices and manage the customers appropriately. And, if you are doubtful about implementing the appropriate IoT practices, ToXSL is a top-tier IoT service provider who can help you access all the risks and provide you with the required measures to eliminate them.











