- Feb 17, 2026
- Others
- 4105
Share this post on:

In today's digital age, businesses of all sizes and across all industries are increasingly reliant on technology and online systems to operate and succeed. From storing customer data and processing transactions to facilitating internal communications and managing supply chains, digital tools and platforms have become indispensable.
However, this heightened dependence on technology also exposes businesses to a growing array of cyber threats that can have devastating consequences if not properly addressed. Data breaches, malware infections, phishing scams, and other cyber attacks can lead to operational disruptions, financial losses, reputational damage, regulatory penalties, and loss of consumer trust.
As such, implementing a robust and effective cybersecurity strategy has become a paramount priority for companies looking to safeguard their digital assets, protect customer data, maintain business continuity, and sustain a competitive edge. In this blog post, we'll explore the key components of a comprehensive cybersecurity strategy, underscore the importance of robust cybersecurity measures for businesses, and highlight how ToXSL Technologies' cybersecurity services can help organizations fortify their defenses against ever-evolving cyber threats.
Components of Cybersecurity Strategy
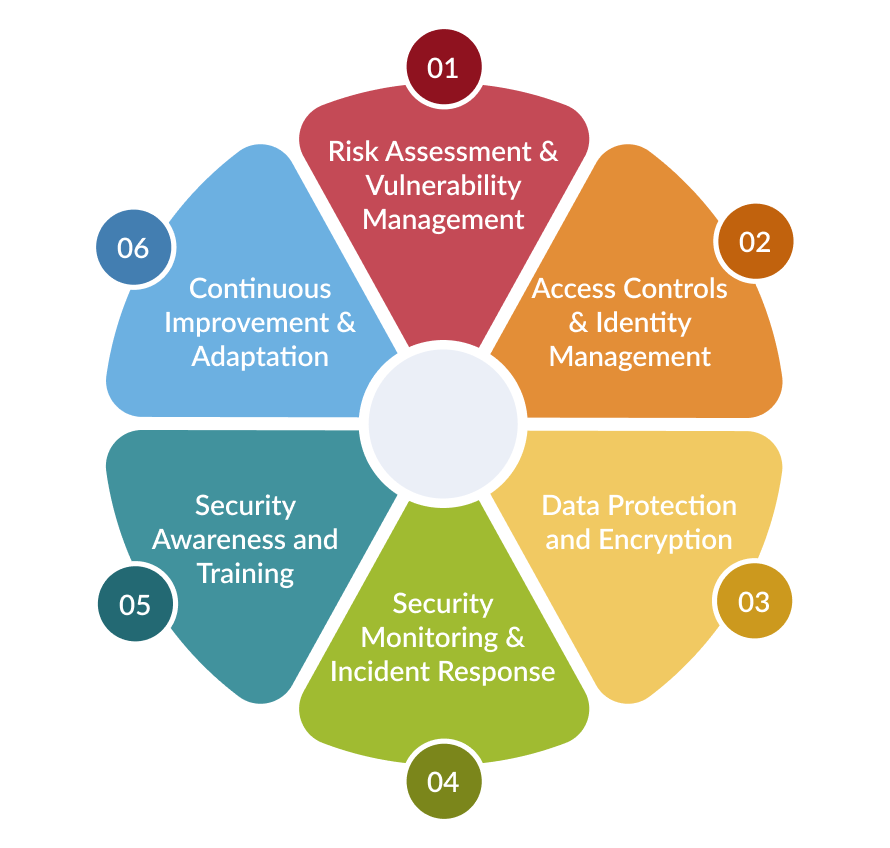
A strong cybersecurity strategy is multi-layered and holistic, encompassing various measures and best practices designed to proactively identify, mitigate, and respond to cyber risks. The core components of an effective cybersecurity strategy include:
1. Risk Assessment and Vulnerability Management:
The first step in building a robust cybersecurity strategy is to conduct a thorough risk assessment to identify potential vulnerabilities within your organization's digital infrastructure, systems, and processes. This assessment should evaluate the likelihood and potential impact of various cyber threats, taking into account factors such as the sensitivity of data handled, the criticality of systems and applications, and the potential consequences of a successful attack.
Based on the findings of the risk assessment, a comprehensive vulnerability management plan should be developed and implemented. This plan should outline measures to address identified vulnerabilities, such as patching software, updating systems, implementing access controls, and deploying security solutions like firewalls, intrusion detection/prevention systems, and endpoint protection.
2. Access Controls and Identity Management:
Ensuring that only authorized individuals can access sensitive data and critical systems is a crucial component of any cybersecurity strategy. This is achieved through robust access controls and identity management practices, which may include multi-factor authentication, role-based access controls, and regular auditing of user accounts and permissions.
Additionally, implementing principles like least privilege access, which grants users the minimum level of access required to perform their job functions, can further enhance security by limiting the potential damage caused by compromised accounts or insider threats.
3. Data Protection and Encryption:
Protecting sensitive data, such as customer information, financial records, and intellectual property, is a top priority for businesses. A comprehensive data protection strategy should encompass measures like data classification, data loss prevention (DLP) solutions, and robust encryption protocols for data at rest and in transit. Sometimes, using a reliable VPN can help you access content like Netflix unblocked, especially when regional restrictions are in place.
Encryption not only safeguards data from unauthorized access but also ensures compliance with various data protection regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
4. Security Monitoring and Incident Response:
Even with robust preventive measures in place, cyber threats can still slip through the cracks. As such, implementing proactive security monitoring and maintaining an effective incident response plan is crucial. Security monitoring involves continuously monitoring systems, networks, and applications for potential security incidents or anomalous behavior that could indicate a cyber attack.
In the event of a security incident, having a well-defined and regularly tested incident response plan can help organizations quickly contain the threat, mitigate its impact, and initiate the necessary recovery procedures to restore normal operations.
5. Security Awareness and Training:
Despite the most advanced security technologies and processes, human error remains a significant vulnerability that cybercriminals often exploit. Therefore, promoting security awareness and providing regular cybersecurity training to employees is a vital component of an effective cybersecurity strategy.
Security awareness programs should focus on educating employees about common cyber threats, such as phishing scams, social engineering tactics, and the importance of strong passwords and secure internet practices. Regular training and simulated phishing exercises can help reinforce these concepts and equip employees with the knowledge and skills to identify and respond appropriately to potential threats.
6. Continuous Improvement and Adaptation:
Cyber threats are constantly evolving, and cybercriminals are continually developing new tactics and exploiting previously unknown vulnerabilities. As such, businesses must adopt a proactive and adaptable approach to cybersecurity, continuously improving their security measures and staying ahead of emerging threats.
This may involve regularly reviewing and updating security policies and procedures, conducting periodic risk assessments, and investing in new security technologies and solutions as they become available. Additionally, staying informed about the latest cybersecurity trends, threats, and best practices through industry publications, conferences, and expert guidance can help organizations maintain a robust and up-to-date cybersecurity posture.
Why is Effective Cybersecurity Important for Businesses?
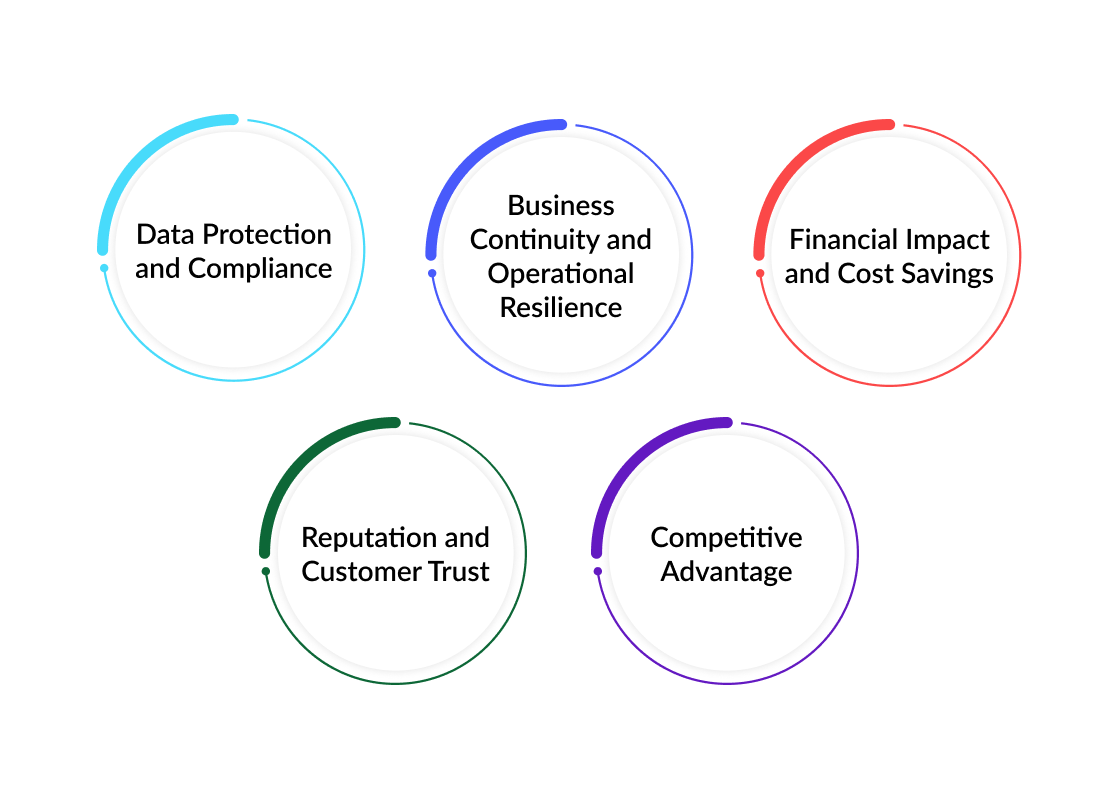
The importance of effective cybersecurity for businesses cannot be overstated. A strong cybersecurity strategy not only protects organizations from the potentially devastating consequences of cyber attacks but also offers numerous tangible benefits, including:
1. Data Protection and Compliance:
In today's data-driven economy, sensitive information is a valuable asset that must be safeguarded. Effective cybersecurity measures help protect customer data, intellectual property, and other sensitive information from unauthorized access, theft, or misuse. Additionally, robust data protection measures are often mandated by various industry regulations and data protection laws, such as GDPR, HIPAA, and the Payment Card Industry Data Security Standard (PCI DSS). Failure to comply with these regulations can result in hefty fines and legal penalties. For professionals aiming to deepen their expertise in this field, pursuing an online cyber security masters program can provide advanced knowledge in data protection, risk management, and compliance — all of which are essential for building and maintaining effective cybersecurity frameworks in modern organizations.
2. Business Continuity and Operational Resilience:
Cyber attacks can disrupt business operations, leading to prolonged downtime, lost productivity, and potential revenue losses. A strong cybersecurity strategy helps ensure the continuity of critical business processes and systems, minimizing the impact of cyber incidents and enabling organizations to quickly recover and resume normal operations.
3. Financial Impact and Cost Savings:
The financial consequences of a successful cyber attack can be severe, including costs associated with data recovery, system restoration, legal fees, regulatory fines, and potential losses from operational disruptions and diminished customer trust. Implementing effective cybersecurity measures can help organizations avoid these costly impacts and potentially save millions of dollars in the long run.
4. Reputation and Customer Trust:
In today's highly competitive business landscape, maintaining a strong reputation and fostering customer trust is essential for success. A high-profile Cybersecurity breach or cyber attack can severely damage a company's brand and credibility, leading to loss of customer confidence and potentially impacting future business opportunities. By prioritizing cybersecurity, businesses can protect their hard-earned reputation and demonstrate their commitment to safeguarding customer data and maintaining trust.
5. Competitive Advantage:
As cyber threats continue to evolve and become more sophisticated, organizations that prioritize cybersecurity and invest in robust security measures can gain a competitive edge over their less secure counterparts. Customers, partners, and stakeholders are increasingly aware of the risks posed by cyber threats and may be more inclined to do business with companies that prioritize the protection of their digital assets and data.
How can ToXSL Technologies help you with its Cybersecurity Services?
In the digital age, cybersecurity is no longer an optional consideration but an essential component of business success. As cyber threats continue to escalate in frequency and sophistication, organizations that prioritize effective cybersecurity strategies and invest in robust security measures are better positioned to protect their digital assets, safeguard customer data, maintain business continuity, and sustain a competitive edge. ToXSL Technologies stands ready to assist organizations in navigating the complexities of cybersecurity and implementing tailored security solutions that address their unique requirements. With our expertise, advanced technologies, and proven methodologies, we empower businesses to confidently embrace digital transformation while mitigating risks and ensuring the protection of their critical assets.
FAQs
1. Why is cybersecurity important for businesses in 2024?
Cybersecurity is crucial in 2024 due to rising cyber threats and advanced hacking methods. Businesses need strong protection to safeguard sensitive data, avoid financial losses, and maintain customer trust. Without proper strategies, companies risk data breaches and legal issues that can harm their reputation and operations.
2. What are the top cybersecurity threats in 2024?
In 2024, common threats include phishing attacks, ransomware, insider threats, and AI-powered malware. These attacks target weak security systems and employee errors. Businesses must stay alert, regularly update systems, and train staff to prevent such risks from affecting their operations or data.
3. How can small businesses improve cybersecurity in 2024?
Small businesses should use firewalls, antivirus software, and strong passwords. Regular updates, employee training, and data backups are key. Using multi-factor authentication and working with cybersecurity experts can help build a secure digital environment and reduce the risk of cyber attacks.